You can now view, reply, and favourite posts from the Fediverse. You can click here or click on the on the navigation bar on the left.
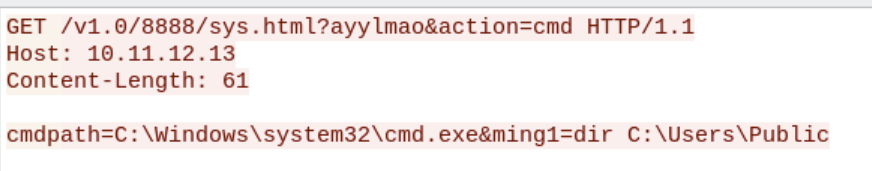
today I've learned that GET requests can technically have a request body.
Uncategorized
1
Posts
1
Posters
0
Views
-
today I've learned that GET requests can technically have a request body. In most normal cases, the server ignores the client body on the get request.
Additionally if a content-length header is specified and you include a body on a GET request, that Snort2.9 and Suricata5+ will inspect the client body.
why do I bring this up?
This is a great write-up by ESET on GhostRedirectory and their Rungan backdoor:
I forged this pcap, and got my rule to fire:
alert http any any -> $HOME_NET any (msg:"ET MALWARE GhostRedirector Rungan Backdoor Access M1"; flow:established,to_server; http.method; content:"GET"; http.uri; content:"action|3d|cmd"; fast_pattern; http.request_body; content:"cmdpath|3d|"; content:"ming1|3d|"; reference:url,www.welivesecurity.com/en/eset-research/ghostredirector-poisons-windows-servers-backdoors-side-potatoes/; classtype:trojan-activity; sid:1; rev:1;) -
R AodeRelay shared this topic